Reporting and Tracing Birthright Entitlement Assignments
Overview
Once birthright entitlements are configured in EmpowerID, administrators will often need to investigate and verify who has access to specific resources, how those assignments were made, and whether they are inherited or directly assigned. EmpowerID provides several tools and interfaces for tracing and reporting access assignments, whether you're looking at a resource, an actor (like a role), or a specific person.
This document guides students through the different tools available in EmpowerID for reporting and auditing entitlements, with practical examples for tracing access back to its origin.
Tracing Group Assignments from the Resource View
In the Classic Admin interface, begin by navigating to Identity Administration > Groups, and search for the group you want to inspect—e.g., Asset Management File Shares. Open the group and go to the Advanced tab. Under RBAC, then RBAC Access to This Resource, select Resource Delegations to view which actors (such as Business Roles and Locations or Management Roles) have access to the group.
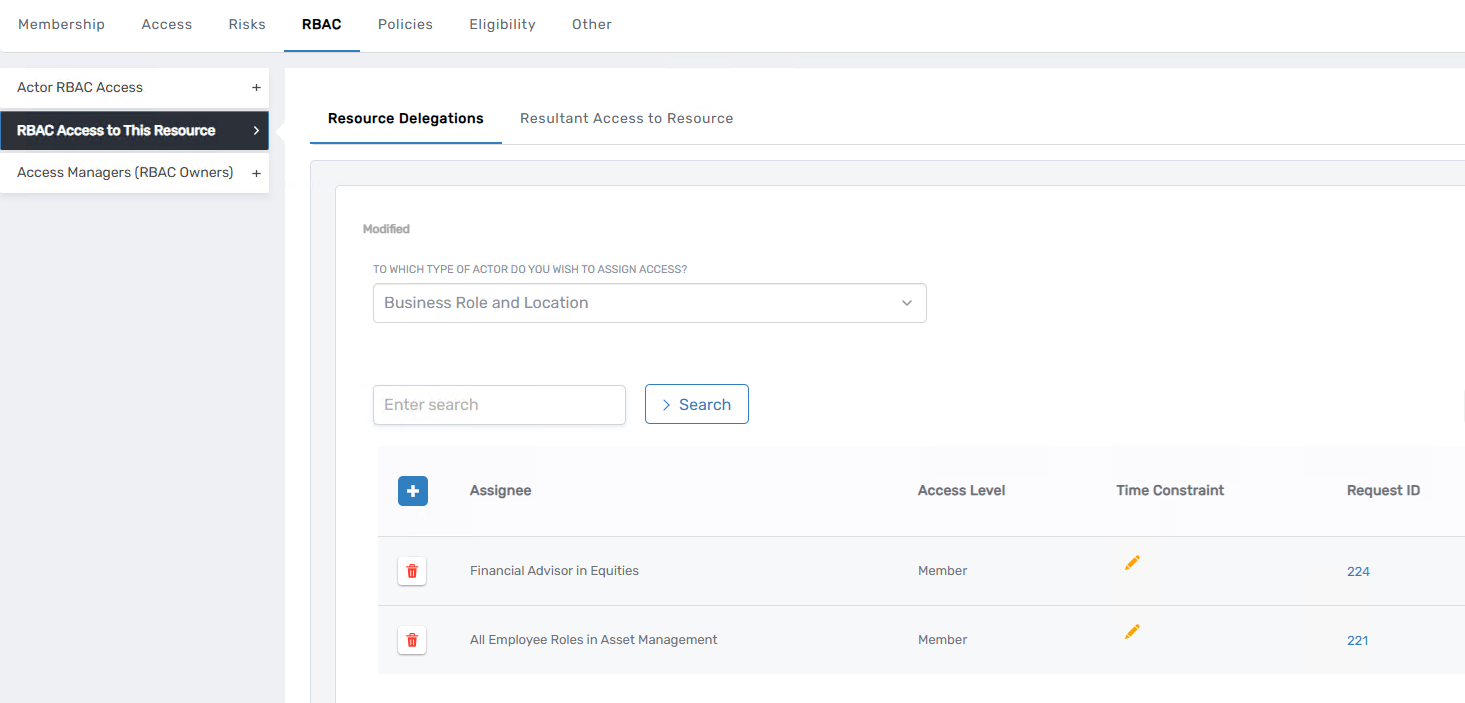
The Resource Delegations tab only displays direct assignments—it does not show inherited access. For example, if the group is directly assigned to the “Financial Advisor in Equities” business role, this will appear here. You may also see assignments to management roles, such as “Asset Management Basic Permissions.”
Viewing Resultant Access (Who Actually Has Access)
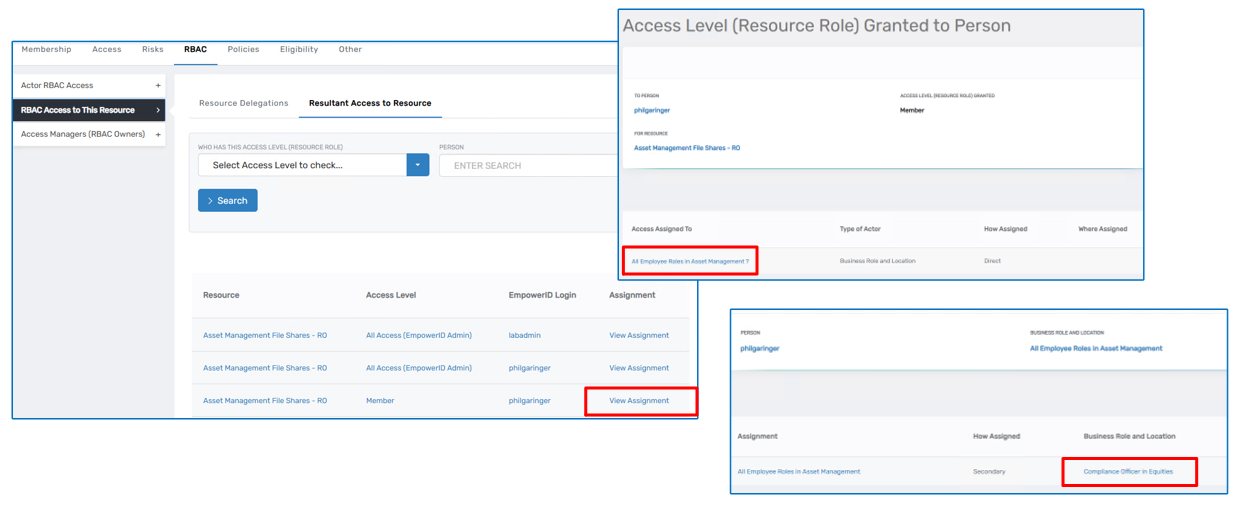
To see the individuals who are effective members of a group (including via inheritance), use the Resultant Access to This Resource link. This screen displays the final set of users who have access, based on all direct and inherited assignments.
Clicking View Assignment for a person will show how that access was granted. For example, a user may have received membership because their assigned role (e.g., “Fixed Income Analyst in Fixed Income”) is a child of a business role and location that was assigned the group. This lets you trace access all the way back to the root RBAC actor.
You can filter the results by access level (e.g., Member, All Access) or search for a specific person to determine whether and how they have access to the resource.
Tracing Assignments via Management Role
When a person has access due to a management role assignment, you can trace this in the same Resultant Access screen. For example, if a person has “All Access” to all groups, it may be because they are directly assigned to a system-wide administrator management role. By following the assignment trail, you can see that their person object was added as a direct member of that management role, and that role grants full group access.
If needed, this is also the point where you can remove or investigate the root assignment, such as a direct membership to a management role, without editing the resource itself.
Global Delegation Views
For broader reporting, you can use the Manage Delegations page. This tool provides two modes:
- Actor Delegations: View all assignments granted to business roles, management roles, and other actors.
- Resource Delegations: View all actors who have access to a specific resource.
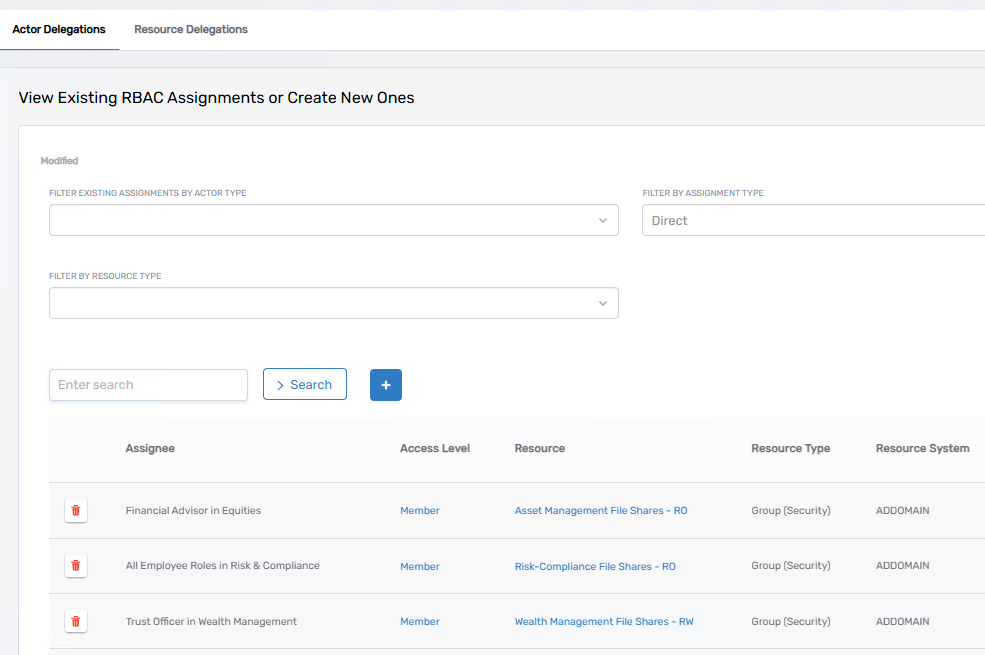
Using these modes, you can filter by actor type, such as Business Role and Location, to see what group memberships are granted to which BRLs. You can also filter by resource type (e.g., Security Groups, Mailboxes, Management Roles) to drill into specific types of access assignments.
For example, filtering actor delegations by “Business Role and Location” will show all groups assigned to business roles. Changing the filter to “Management Role” will reveal even more entries, including system-defined role bundles.
Using System Reports for Comprehensive Auditing
Under System Logs > Reports, there is a report titled All Access Assignments in the System. This report displays every RBAC-based security assignment and includes columns for assignment type, object type, resource type, and access level.
For instance, the report may show that the group HR Documents Access is assigned to the Executive Reports group with the access level of Member. This indicates a group-to-group assignment and shows both the actor and the resource involved.
This report can be downloaded to Excel, allowing you to sort, filter, and analyze assignments offline using pivot tables or other reporting tools. It’s especially useful for organizations needing a full snapshot of all entitlement configurations.
Conclusion
EmpowerID provides robust capabilities for tracing and auditing entitlement assignments. From tracing a specific user’s group access to analyzing full-system access reports, administrators have multiple tools at their disposal. These interfaces not only support compliance and auditing needs but also provide insight into how and why access is granted—helping ensure security and clarity in identity management.